What is a Phishing Attack in Cybersecurity Nowadays?
Digital technology is being used more than ever before. It has made tasks easier for people. For example, messages that used to take one or two months to arrive now reach in just a few seconds. Similarly, businesses now rely on technology and store their important information in digital systems, which can be of various types.
Some people are aware of cyberattacks, but most are not. They do not take the necessary security steps to protect their data from hackers, such as using security tools. Because of this, they fail to keep their data safe, and hackers easily steal their information.
Earlier, I talked about basic cybersecurity and malware. Now, I will explain what a phishing attack is and how hackers trap people in their scams.

Understanding What is a Phishing Attack in cyber security?
Phishing Attack: A phishing attack is a type of cyber attack in which a hacker deceives you using technology and steals your personal information, meaning your personal data that you save in your system, such as bank account numbers, credit card details, and other sensitive information. May try to steal.
Phishing attacks can trick you in any way. Such as fake emails, cloned websites, or misleading links.
- A friend of mine has an example: I had a friend; a guy came to him and said, “Join this link; I will get 2000 rupees, and you will get 1000 rupees. Just join; I have joined 3 people; only 1 person is left; you join.”
My friend, believing his words, clicked on the link and joined the WhatsApp group. Suddenly, at night, messages started coming automatically on his WhatsApp, which were in Portuguese. My friend thought that in the morning I would show someone what was happening, but by morning his WhatsApp had been hacked.

Don’t think that you can be scammed by a link. You can also be scammed by a fake website. Also via email.
When you open these links or download something from a website, hackers install malware on your system. Which gives the hacker full control of your system. The hacker can operate your system wherever he is. Any detail in the system can be stolen by a hacker.
- Social Engineering & Phishing
Social engineering is a cyber attack in which the hacker does not use any of his own techniques to hack but rather obtains information from people by deceiving them; that is, he tries a tactic through which people give up their information themselves.
- Example: Your business is import and export. You make payments to someone, sometimes through an app or by going to the bank and doing it online.
What a hacker does in social engineering is send you a fake email. That email looks like it came from a bank. It says that there is a problem with your account. Please click on this link button. When you click on this button, a page opens in front of you in which you are asked to type your name, email, and password. This is a method of social engineering to trick people and get their information.
7 Types of phishing attack in cyber security
I told you about phishing attack in cyber security; now I will tell you about their types.
- Email Phishing
- Spear Phishing
- Whaling
- Vishing (Voice Phishing)
- Smishing (SMS Phishing)
- Clone Phishing
- Angler Phishing
I’m telling you about the types of phishing so that you know how each type of attack works.
Email Phishing:
This is the most common type in which a hacker sends you an email that looks like it came from a bank or company, but you are tricked by the hacker. When you open it, malware is installed on your system. As soon as it is installed, your system hangs and your system is shut down, but a backdoor to your system is opened for the hacker.
Spear Phishing:
This is a little more dangerous than a typical phishing email in that it targets a specific person and attacks them.
For example, if you are in a company and receive an email saying something like “Hello (John), I am from your company’s IT department. Please click on the link below.” And update your login details. This attack is done by pretending to be your friend or company member so that you don’t suspect anything.
Whaling:
This is a type of phishing attack that targets big names like CEOs and company owners.
for example: A man has a very large company and has four to five other branches. Attack and will contact one of the same companies, saying I want to get the details of your owner. I am a bank employee; there is a problem with their account. I want to meet them, or do you have any contact number or any email through which I can contact them?
When an attacker gets even a small piece of information, he can extract all your details through it.
Vishing (Voice Phishing)
This is also the same phishing method in which the victim is tricked through attacks and calls that I gave you as an example. In whaling, it works in the same way to obtain information.
Smishing (SMS Phishing)
This is also the same method in which the hacker tricks you through SMS or text messenger to click on a link. When you click on it, you are taken to a fake website or malware page, through which the hacker can easily steal your information from your system.
Clone Phishing
In this attack, the attacker converts the original email into a duplicate email and sends it to you. Because you are aware of this email that it is the same email that you have received from the company before, you open this email and become a victim of the attack.
Angler Phishing
These attacks are carried out through social media or platforms that make you believe that it is actually someone who wants to get our information for some purpose, but it is not. These are other attacks that use social media platforms to get your information. For example, if I am talking about a representative of a certain company, some calls, emails, and SMSes come to you, which deceive you, and you give them your information.
Now you must understand. What is phishing attack in cyber security? Now I will tell you. How to Protect Against phishing attacks
How to Protect Yourself from Phishing Attacks?
You have found out how cyber attacks occur in phishing and what their types are. Now I will tell you what you need to do to avoid them.

Basic safety measures
When you receive an email or SMS that you are suspicious of, do not open it, but rather hover over it and search for the URL or search for the suspicious link or message directly in the browser to check whether the site or link is genuine.
Hackers often create fake links that can trick you.
🚫 www.paypa1.com (Fake) ✅ www.paypal.com (Original)
🚫 www.goog1e.com (Fake) ✅ www.google.com (Original)
Sometimes hackers create email addresses that look like real companies to trick people.
For example
🚫 support@paypalsecurity.com (Fake) ✅ support@paypal.com (Original)
🔹 Use strong and unique passwords:
Don’t always use the same password everywhere. Wherever you have accounts, their passwords should be different. They should be strong, at least 12 characters long.
For example
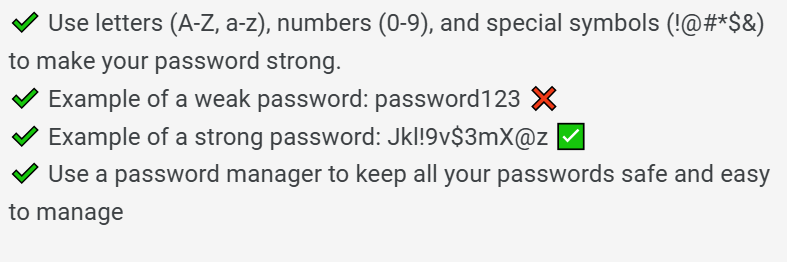
Technical safeguards
🔹 Use Two-Factor Authentication (2FA)
For example
2FA is an additional security system. When you open the system and enter your password, another page opens in front of you in which you have to add four to five word numbers, which are called OTP, which comes to your mobile number. This method is 2FA, which makes your system more secure and no one can hack it or receive information. This process is available in your system because whenever you set a password, you are additionally told to enter a recovery email or enter your number in it.

🔹 Use of email spam filters and firewalls
Activate the spam filter in your system. What is a spam filter? When a mail or link arrives in your mailbox, it verifies it all. If it finds a suspicious link, it filters it and removes it from your mailbox.
Use malware and antivirus software on your system to avoid malicious email links. Always keep your system and browser antivirus software updated to eliminate security vulnerabilities. What hackers do is often attack systems whose software is not updated, so always keep your software system and browser updated.

Conclusion
Adopt cybersecurity measures to protect yourself from phishing attacks.
In this post, I have shared my experiences with you, which I often share with others to help them stay safe from phishing attacks. I have given you tips on how these attacks can harm you and how you can protect yourself from hackers.
Yes! To keep your online security safe, follow these precautions and protect your data from hackers.
If you have any questions or face any issues, feel free to ask me in the comment box without hesitation.
FAQ
What is a phishing attack in cyber security?
A phishing attack is a type of cyber attack in which a hacker deceives you using technology and steals your personal information, meaning your personal data that you save in your system, such as bank account numbers, credit card details, and other sensitive information.
Where Are Spam Filters Used?
Spam filters help block unwanted and harmful emails, keeping your inbox clean and secure. They are commonly used in:
📌 Email Services: Platforms like Gmail, Outlook, and Yahoo Mail use spam filters to stop junk emails from reaching your inbox.
📌 Web Hosting: Many website hosting services, such as WordPress and cPanel, include spam protection to prevent malicious emails from reaching website owners.
📌 Business Security Systems: Companies use email filtering systems (like Exchange Servers) to protect their employees from phishing attacks and harmful emails.
Why Should You Keep Spam Filters On?
🚀 If spam filters are turned off, your inbox can fill up with unwanted emails, including scams and dangerous links. Always keep spam protection active to stay safe online!
What to do if a phishing attack?
- If you have discovered that your system has been attacked by a phishing attack, there is no need to panic. You should immediately change any passwords you have set. If you have logged in to a fake website link or email, change the passwords for all affected accounts.
- If the phishing attack is related to your bank account or social media account, call your bank’s helpline immediately. And report it to the official website of the social media you are using.
- Scan your entire system to detect malware as soon as possible.
- The sooner you act, the sooner you can save your system.
More Information Click Here



Appreciation to my father who told me regarding this
website, this weblog is genuinely awesome.
thanks
good
nice
The article provides some great advice on the topic. Thanks for sharing your experience with us.
Love the unique perspective you offer to this subject.